Hopefully, you are fully aware of what Cisco Identity Intelligence is. If not, take a look at this blog post. In short, it's a fantastic solution for Identity Threat Detection and Response (ITDR). When a detection fires in Cisco Identity Intelligence (CII); which is to say that a user or login event triggers a failed … Continue reading Cisco Identity Intelligence – Webhooks with Cisco XDR
My Enthusiastic Return to Identity
Some History To Set the Stage Why am I so excited to return to Identity Security as a primary focus? Around 8 years ago I made a very difficult decision to leave my "baby" behind, and move from the Identity Services Engine (ISE) team - and head off to something new and exciting: Threat Detection … Continue reading My Enthusiastic Return to Identity
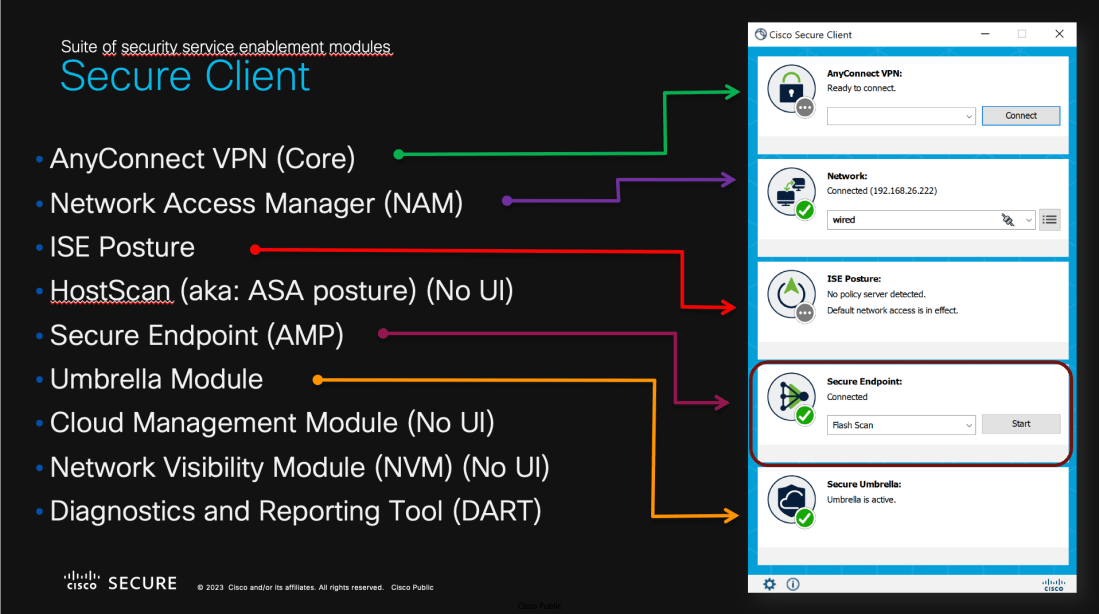
Hiding the Secure Client aka: AnyConnect VPN Module
How to hide the VPN module in Cisco Secure Client, formerly known as AnyConnect.
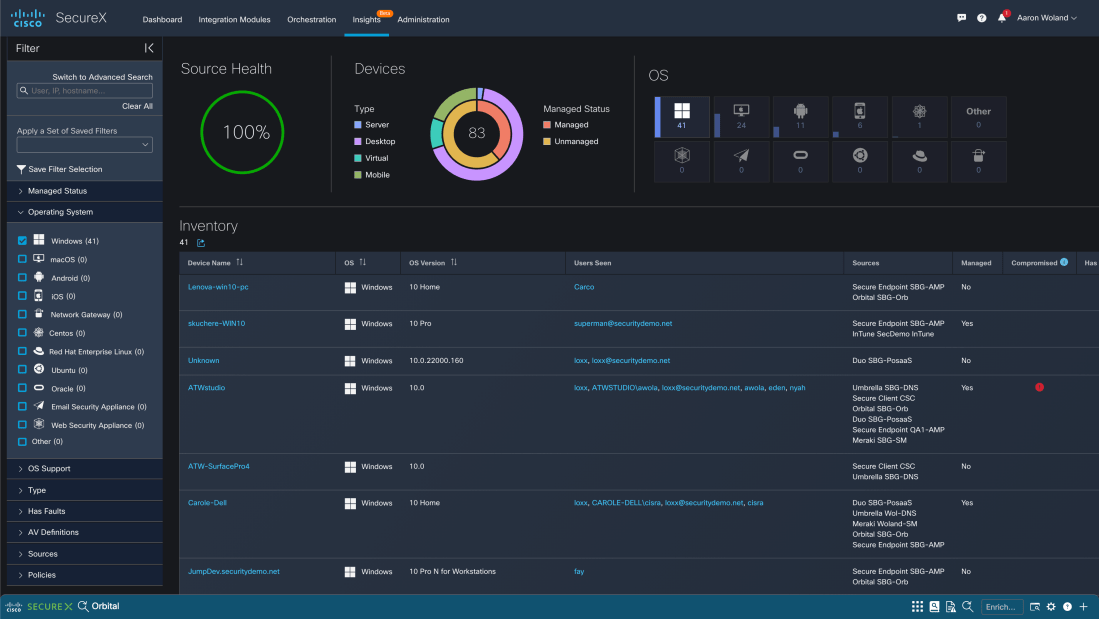
Introducing SecureX Device Insights – Looking for Testers
SecureX is something that was a long-time-coming and very welcome now that it’s here. Cisco now has a centralized, cloud-based, integration platform to act as a hub for the plethora of security products in the Cisco portfolio as well as with non-Cisco security products as well! With this centralized platform approach, there are many functions … Continue reading Introducing SecureX Device Insights – Looking for Testers
Posture w/ ISE & Mobile – the stuff no one talks about
I recently presented a CCIE Security webinar on this topic because it's a topic that is poorly documented and even not very well understood. Naturally, that is something I want to change, and the exact type of thing that this blog is exists for! This blog post will dive into how ISE works with mobile … Continue reading Posture w/ ISE & Mobile – the stuff no one talks about
Dynamic Split Tunneling – a COVID-19 Best Practice
I'm posting this blog with intentions of helping you with some best practices around your Cisco AnyConnect Remote-Access VPN (aka: RA-VPN) configuration. With these best practices, I will try to include the different thought-patterns around "why" a company might choose to deploy 1 way or another, but my recommendations will still stand as MY best practice, which also matches what the AnyConnect business unit at Cisco recommends, as well.
What Zero Trust really is and what it isn’t.
Brief understanding of what Zero Trust is, what the history is that got us where we are today, and what gap exists between true ZT & the capabilities in the industry today.
Security of the Modern Mobile OS
The idea for this blog post came to me during a discussion around some recent research performed by Cisco's Talos threat research group. The post: Advanced Mobile Malware Campaign in India uses Malicious MDM authored by Warren Mercer, Paul Rascagneres and Andrew Williams and the follow-up post containing additional research found here: Part-2. In this … Continue reading Security of the Modern Mobile OS
Using Configurator 2 to prep iOS for CSC
In order to use Cisco Security Connector (CSC) for iOS, the endpoint must first be in supervised mode and managed by an MDM. The easiest way to manage Apple iOS devices is to use Apple's Device Enrollment Program (DEP); which is now rolled into their new Apple Business Manager (ABM) program. However, there are certainly … Continue reading Using Configurator 2 to prep iOS for CSC
Configuring Notifications with Cisco AMP
So I am often asked this question, so I figured I would blog it & then be able to just send a link to the blog to the next person(s) who ask this question. The magic question I'm referring to is: "how do I configure an email notification for events in AMP". I guess I … Continue reading Configuring Notifications with Cisco AMP


You must be logged in to post a comment.