
Some History To Set the Stage
Why am I so excited to return to Identity Security as a primary focus?
Around 8 years ago I made a very difficult decision to leave my “baby” behind, and move from the Identity Services Engine (ISE) team – and head off to something new and exciting: Threat Detection & Response.
Threat Detection & Response is a great place to be! Preventative security measures just aren’t preventing enough, which leads the industry to Endpoint Detection & Response (think Cisco Secure Endpoint (aka: AMP), Crowdstrike and others. The industry also moves into Network Detection & Response (think Cisco Secure Analytics, Darktrace & others).
However, identity was sorely missing, and yet becoming one of the top attack vectors.
I was asked to be one of the leaders for the effort of defining Cisco’s strategy for Identity Threat Detection & Response (ITDR), which is where this story is really going to begin.
April 2023: “Tom Gillis has re-entered the room”…
Tom comes back to lead Cisco Security as the SVP & General Manager, and he comes back with the drive and power to make a few amazing acquisitions!! You might have heard of Armorblox, Isovalent, and Oort (let’s not mention that small one named Splunk 🙂 ).
We are going to focus on Oort! Why? Because this is the company that I begged Tom to acquire. But, why Oort?
ITDR is a brand new space. It doesn’t even have a magic quadrant yet. What it has is pioneers, and Oort is one of the early pioneers who was already viewed as a leader in this up & coming space. Not only are they a leader there, the entire company is made up of the “best in the biz”.
Leading the company was Matt Caulfield (CEO) & Didi Dotan (CTO). Now, I had never worked with Matt prior to our acquisition of Oort, but Didi & his entire team were the engineering organization that build “Device Insights” with me – before leaving for the Oort startup. I knew them VERY well, I knew the quality of their work and the absolute incredible talent involved in that small company.
We (Cisco) really ran the product through its paces during our due diligence period.. We checked into its efficacy, scale – Cisco IT/Infosec even started using the solution at-scale for Cisco’s own Identity Security protections. It performed beautifully & was definitely the greatest thing we evaluated for ITDR.
Getting the Band Back Together
It is no secret that I very much wanted to work with this team again. To be honest, we are more like a “band of brothers [and sisters]” than just co-workers (hey, siblings argue too, you know..).
Well, I’m back. I am now working full-time on Cisco Identity Intelligence (the solution formerly known as Oort). I am here because of how much I believe in this mission, this product and this team.
What is Identity Intelligence (aka: Oort)?
You’ve just ready (or skipped) the history of how we got here. Now let’s discuss what it actually is and does.
Gartner defines ITDR as:
…a security discipline that encompasses threat intelligence, best practices, a knowledge base, tools, and processes to protect identity systems. It works by implementing detection mechanisms, investigating suspicious posture changes and activities, and responding to attacks to restore the integrity of the identity infrastructure…
What I find interesting in Gartner’s definition is how a Detection & Response category is covering both Preventative and Reactive security, not just reactive.
Well, Cisco Identity Intelligence (Oort) is absolutely doing both. note: It is not an inline solution, instead it connects to the organization’s Identity Providers (IDPs), to bring all the identity logs & data into a solution.
Why not just use what’s built into my IDP already?
Most of the organizations that I have worked with over the years do not have just one IDP. There is usually many, and multiple offerings of MFA in the organization too. You may have a first factor of Okta, and 2nd factor of Duo (for example); or maybe a first & second factor of Entra ID (aka: Azure AD) with Microsoft Authenticator.
You cannot get a complete picture of your identity posture, or identity threats from looking at just one of those IDPs. You need a full 360 degree view of the users and any applications they authenticated to, what devices they used to do so, if there is any weak MFA configured across the IdP spectrum.
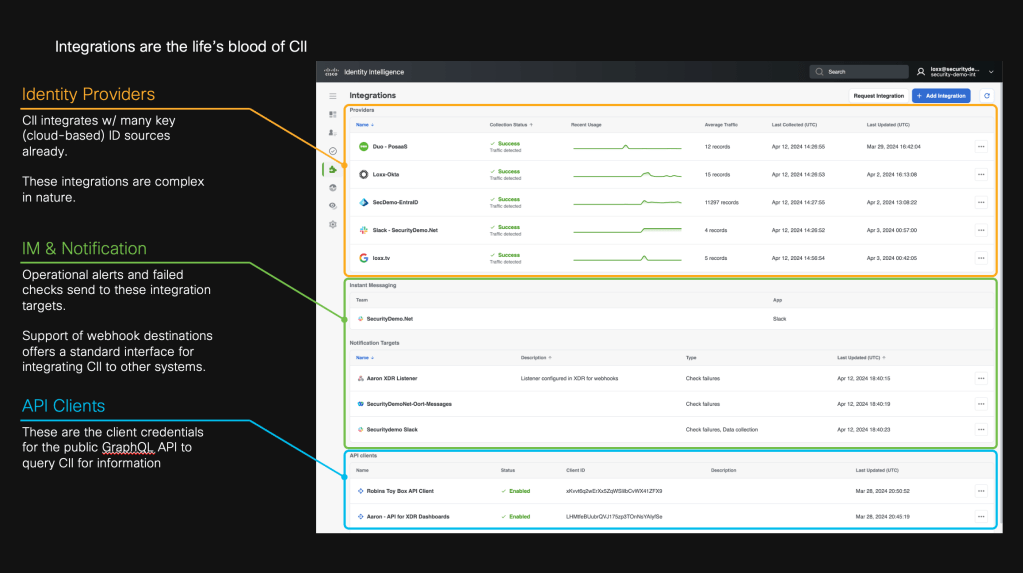
Identity Intelligence (Oort) integrates with your IDPs, bringing over the user data, directory structures, and even streams logs from most IDPs directly into Oort. That data is normalized and it is examined against what we call “checks” to determine threats, posture, compliance and so much more.
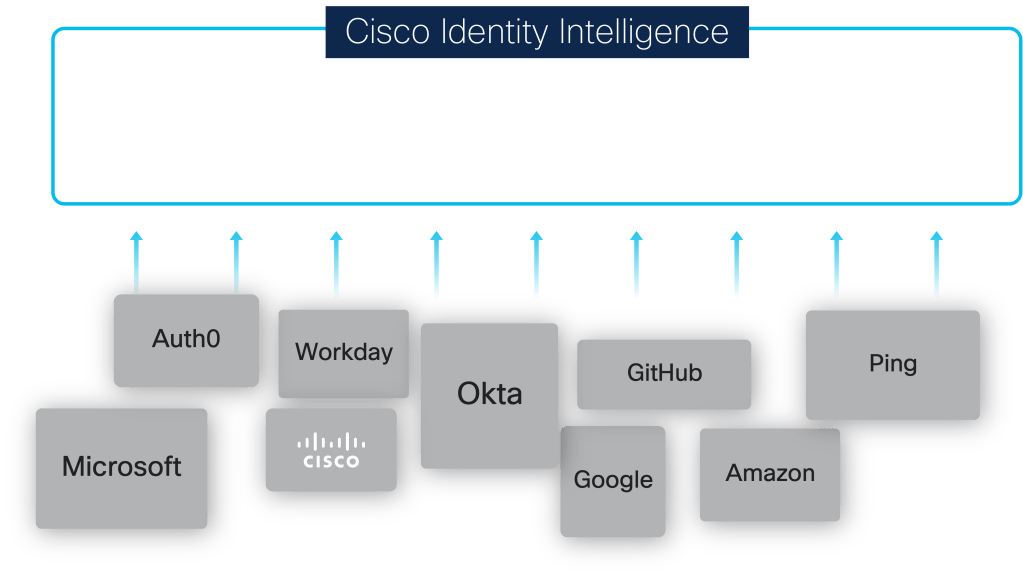
Let’s see those integrations!
Identity Intelligence (aka: Oort) integrates with most cloud-based IDPs including Okta & now Okta Identity Engine (OIE), Microsoft Entra ID (Azure), Duo Security, Auth0, Google Workplace, and more.
But it doesn’t only integrate with IdP sources. It also connects to Human Resource Information Systems (HRIS), collaboration tools, and ticketing systems. It also leverages HTTP/s webhooks to enable alerting external systems such as XDR’s, SIEMs, SOARs, etc.
User360
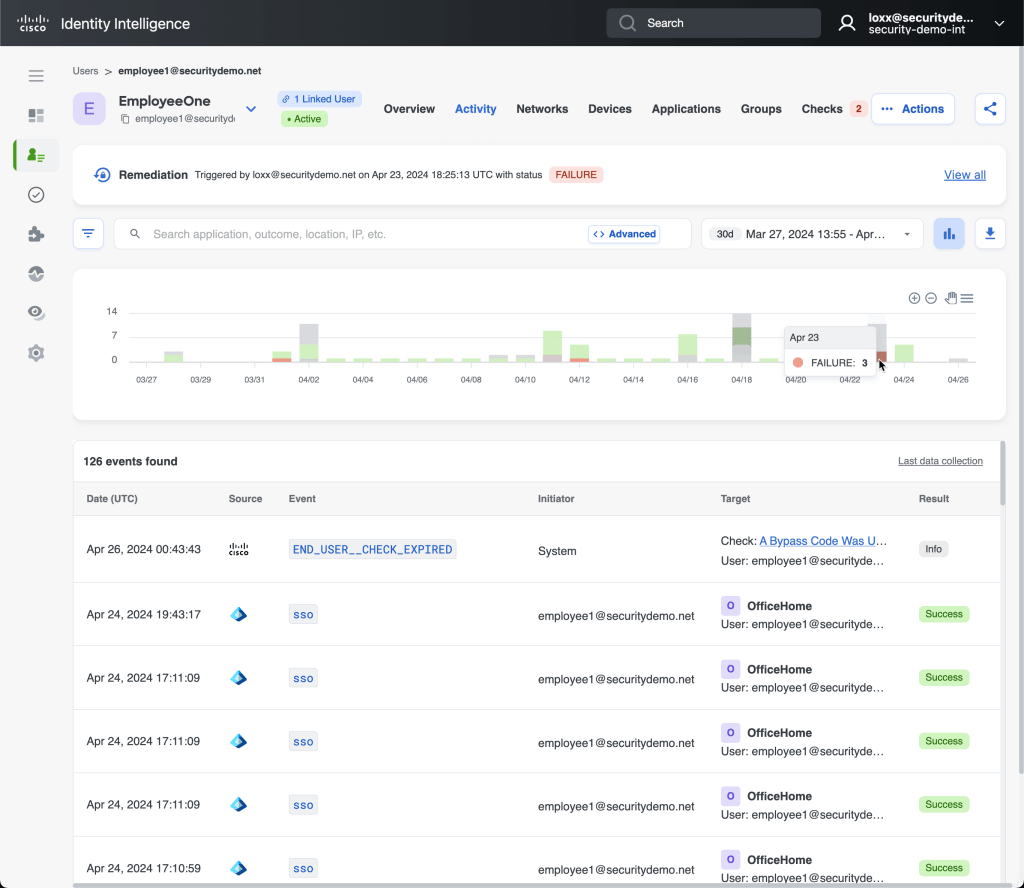
Think about it. You need a single location to view a common identity posture & threats that can span the all the IdPs and apps across your entire organization. That’s what Identity Intelligence brings & it is most obvious when you look at what is called: “User 360”.

This view is incredibly powerful. On the overview page, we can see the employee has failed a check. There is really cool Activity Flow diagram where the abnormal stands out. We get a consolidated view of all the authentications and activities from the disparate IDPs.
Activity
Gives us a view of all the activity, all the authentications and account changes, etc.. Adding MFA types, new account creations, etc..
Networks
Which IP’s has the user been seen using. These are the IPs reported by the IDPs and keep in mind they are often the public IP that’s been NAT’d on its way out to the Internet. It does give us terrific insight into patterns and also if users leverage anonymizers or personal VPN offerings, etc..

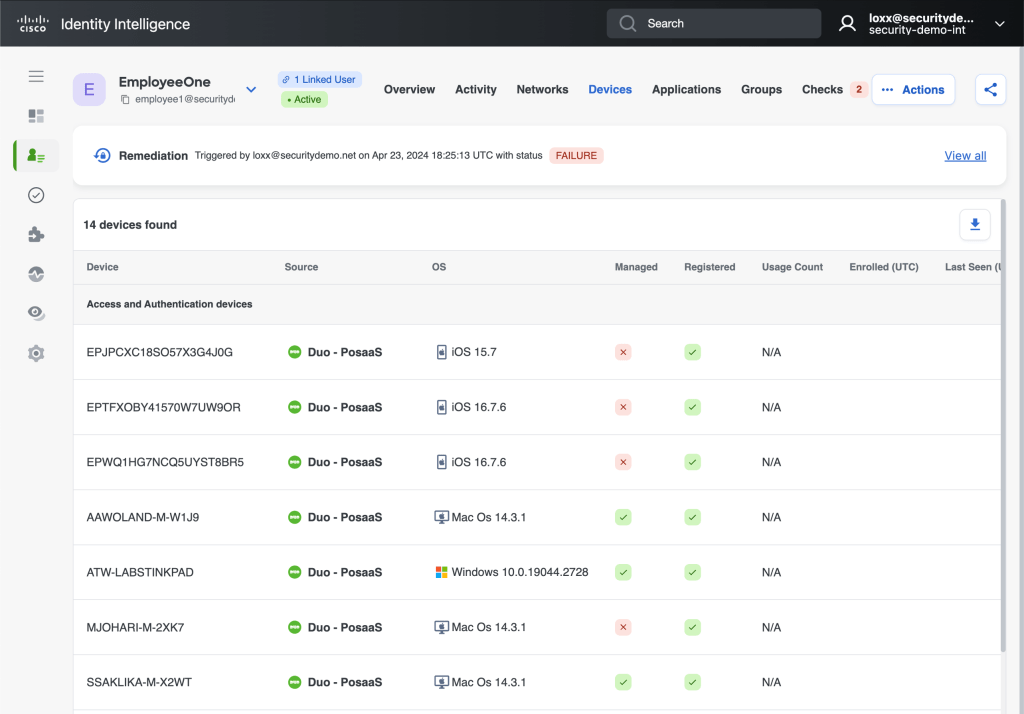
Devices
The access devices – the ones connecting to the App, also the MFA devices like phones, yubikeys, etc.
Applications
Which applications are the IDPs telling us the user is authenticating to. This is based on the definition within the IDPs themselves, and which apps they are authenticating access for. It not only tell Oort which apps a user is connecting to, but Oort also analyses which ones aren’t being used.
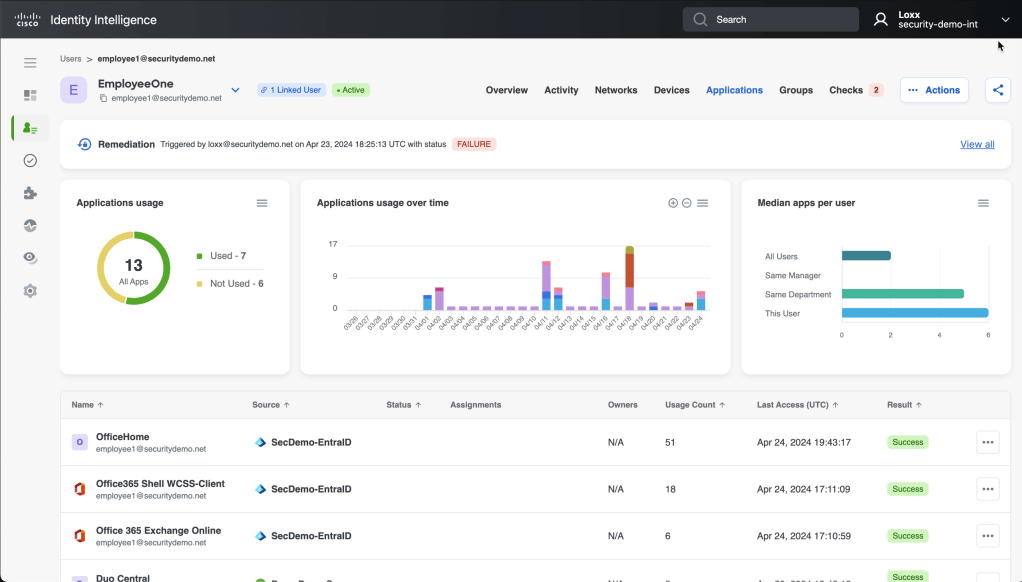
Let’s talk about those “Checks”
I like to equate “checks” to signatures in Intrusion Detection Systems (IDS/IPS). The data collected from Identity Intelligence is processed through what you would equate to as a detection engine; and if the system finds matches on the data to the checks that are being compared – then a user “fails” that check.
In other words checks are looking for things that are wrong. The checks belong to one or more topic such as “Posture” or “Threat”. The checks are also broken down into compliance frameworks.

That’s Enough for Today…
Long story short.. I am ecstatic to be back with a primary focus on Identity Security again, but even more excited to be working with this team on this solution! Look out for more from me on this topic & some new Cisco Live sessions and more!
One thought on “My Enthusiastic Return to Identity”